需求:
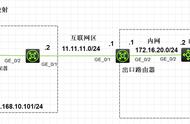
总部固定ip地址,分部PPPOE上网动态获取IP,要求总部分部之间建立IPSEC VPN隧道,内网互通。
拓扑:

配置方法:
基础配置
ISP配置
sysname ISP
interface GigabitEthernet0/0/0
ip address 32.0.0.2 255.255.255.252
interface GigabitEthernet0/0/1
ip address 12.0.0.2 255.255.255.252
interface GigabitEthernet0/0/2
ip address 22.0.0.2 255.255.255.252
PC地址配置
PC1 192.168.1.2/24
PC2 192.168.2.2/24
PC3 192.168.3.2/24
总部出口路由器基础配置:
sysname zb
interface GigabitEthernet0/0/0
ip address 12.0.0.1 255.255.255.252
nat outbound 3000
interface GigabitEthernet0/0/1
ip address 192.168.1.1 255.255.255.0
ip route-static 0.0.0.0 0 12.0.0.2
acl advanced 3000
rule 5 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 10 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 15 permit ip source 192.168.1.0 0.0.0.255
//内网互访地址不做NAT
分部1出口路由器基础配置
sysname fb1
interface GigabitEthernet0/0/0
ip address 22.0.0.1 255.255.255.252
nat outbound 3000
interface GigabitEthernet0/0/1
ip address 192.168.2.1 255.255.255.0
ip route-static 0.0.0.0 0 22.0.0.2
acl advanced 3000
rule 5 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 10 permit ip source 192.168.2.0 0.0.0.255
分部2出口路由器基础配置
sysname fb2
interface GigabitEthernet0/0/0
ip address 32.0.0.1 255.255.255.252
nat outbound 3000
interface GigabitEthernet0/0/1
ip address 192.168.3.1 255.255.255.0
ip route-static 0.0.0.0 0 32.0.0.2
acl advanced 3000
rule 5 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 10 permit ip source 192.168.3.0 0.0.0.255
基础配置完成后内网访问互联网正常
每台PC PING测外网都正常。

IPSEC VPN的配置
由于分部是PPPOE获取的动态IP,总部是无法预先知道分部的地址,因此采用野蛮模式,与分部建立IPSEC VPN通道,并且,只能由分部首先发起访问,才会建立隧道。
为了说明原理,简化掉了PPPOE配置。
总部配置
IKE proposal 1
ike keychain 1
pre-shared-key hostname fb1 key simple 123
ike keychain 2
pre-shared-key hostname fb2 key simple 123
//对端IP事先未知,采用对等体名称配置预共享密钥
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn zb
match remote identity fqdn fb1
proposal 1
//采用IKE野蛮模式
ike profile 2
keychain 2
exchange-mode aggressive
local-identity fqdn zb
match remote identity fqdn fb2
proposal 1
ipsec transform-set tra1
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
ipsec policy-template t1 1
transform-set tra1
ike-profile 1
ipsec policy-template t1 2
transform-set tra1
ike-profile 2
ipsec policy p1 1 isakmp template t1
//采用模板方式配置IPSEC策略,不需要配置感兴趣流
interface GigabitEthernet 0/0/0
ipsec apply policy p1
//出接口应用IPSEC策略
分部1IPSEC VPN配置
acl advanced 3001
rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
//配置访问总部的感兴趣流
ike proposal 1
ike keychain 1
pre-shared-key address 12.0.0.1 255.255.255.255 key simple 123
//总部IP固定,配置相同预共享密钥
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn fb1
match remote identity fqdn zb
proposal 1
ipsec transform-set tra1
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
ipsec policy p1 1 isakmp
transform-set tra1
security acl 3001
remote-address 12.0.0.1
ike-profile 1
interface GigabitEthernet 0/0/0
ipsec apply policy p1
分部2的配置
acl advanced 3001
rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
ike proposal 1
ike keychain 1
pre-shared-key address 12.0.0.1 255.255.255.255 key simple 123
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn fb2
match remote identity fqdn zb
proposal 1
ipsec transform-set tra1
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
ipsec policy p1 1 isakmp
transform-set tra1
security acl 3001
remote-address 12.0.0.1
ike-profile 1
interface GigabitEthernet 0/0/0
ipsec apply policy p1
配置完成后测试分部PC访问总部PC正常

在总部路由上查看IKE sa IPSEC sa信息正常。